Our products
-

SIREN
Security Inventory and Risk Evaluation Network – a software to support compliance, risk- and business continuity management
Learn more ... -

iCompliant
Silent Signal’s proprietary iCompliant tool helps the secure operation and hardening of IBM i (formerly AS/400) systems to minimize the attack surface.
Learn more ... -

Security awareness board game
Our own cooperative security awareness board game can be bought as a product or as a service as well.
Learn more ... -

Awareness Game
Our online Awareness Game can help you bring a new vibe to Cyber Security Month or any other time of the year, to promote security awareness.
Learn more ...
SIREN – Security Inventory and Risk Evaluation Network
Our internally developed SIREN System offers a complex solution for the assessment of business processes, resources and data assets, for performing business impact analysis and risk assessment with various methodologies, and following up on risk mitigation measures as well as supporting business continuity management tasks.
Our solution ensures risk assessment tailored to the organization, unified risk management, and compliance with various internal and external requirements. With the help of SIREN, various surveys can be performed in a simple and user-friendly way, resulting in comprehensible outputs and reports to effectively support managerial decision making.
As its name suggests, SIREN as a Security Inventory and Risk Evaluation Network maps and collects risks resulting from different analyses, compliance requirements, internal and external audits, vulnerability management, incident management and penetration tests into a single channel, providing a full insight of vulnerabilities affecting the organization and information security related tasks.
Business continuity management has its own module, which – beyond identifying critical processes and resources – can also be used for preparing and testing BCP and DRP action plans, with full documentation options. Because of the modular structure of the System, all organizations may pick which functions they need, and the software also makes it possible to import data from other sources, making it easier to review results of previous assessments.
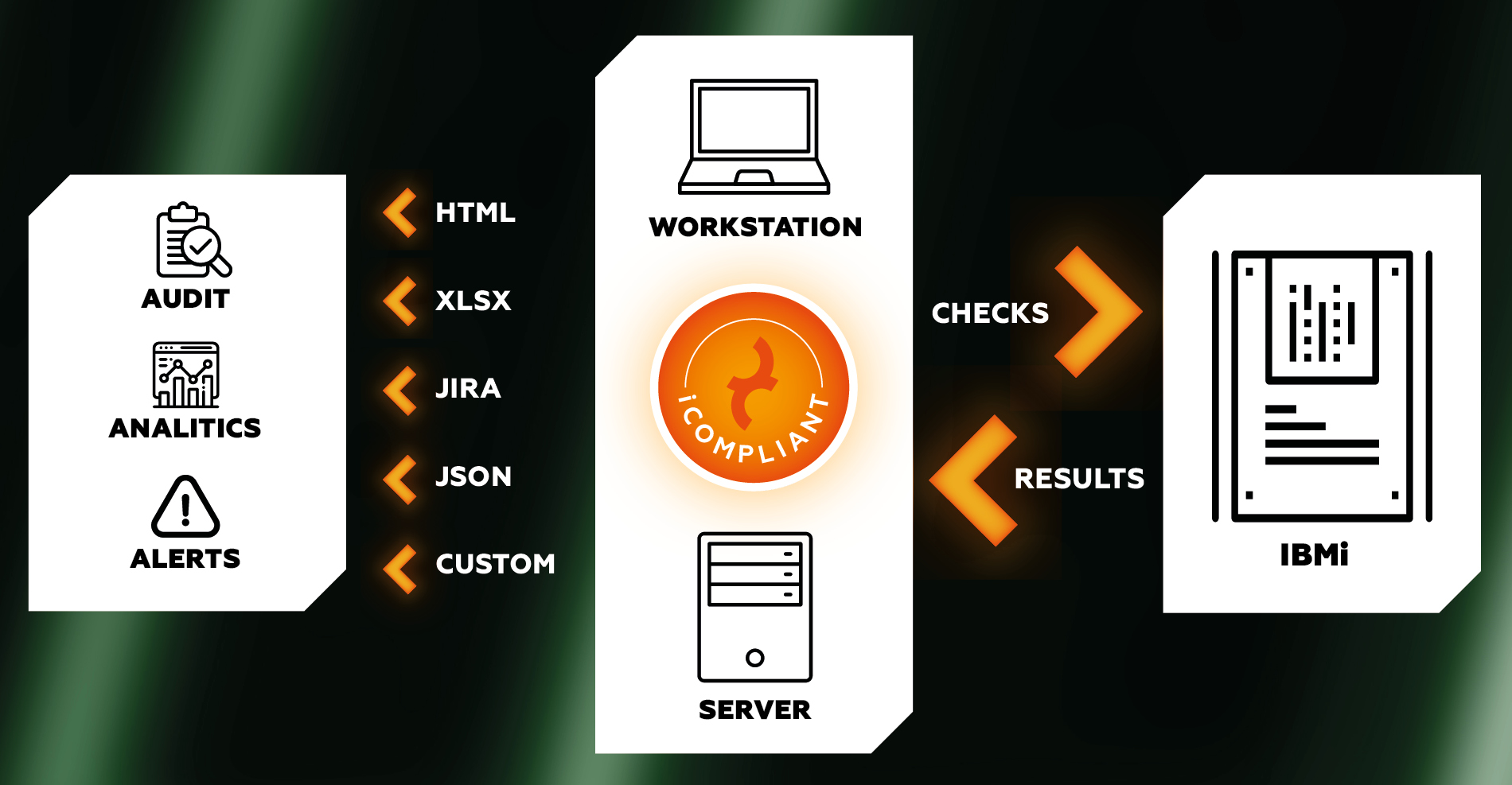
iCompliant – IBM i Configuration Assessment Tool
-
 Assess all aspects of IBM i security from system configuration to object authorization
Assess all aspects of IBM i security from system configuration to object authorization -
 Execute compliance assessments as frequently as needed
Execute compliance assessments as frequently as needed -
 Implement defense-in-depth strategy that reduces the risk of exploitation even if a vulnerability occurs
Implement defense-in-depth strategy that reduces the risk of exploitation even if a vulnerability occurs
IBM i (formerly AS/400) systems play critical role in the business processes of their owners. However, security testing and monitoring of these systems usually doesn’t achieve the level we expect in case of Windows, Linux or Unix hosts.
Silent Signal’s proprietary iCompliant tool helps the secure operation and hardening of IBM i systems to minimize the attack surface. To satisfy the need of in-depth IBM i security assessments, the knowledge integrated into iCompliant is based on multiple pillars:
-
Checks for industry recommendations ensure compliance with security best practices and standards (PCI-DSS, SOX, COBIT, ISO 27002).
-
Hands-on penetration testing experience enables targeted hardening against practical attacks relying on weaknesses outside the usual scope of security standards.
-
The latest results of IBM i security research at Silent Signal are integrated to deliver exclusive defensive solutions.
iCompliant applies this knowledge to examine the overall security posture of its target systems, and deliver comprehensive results about weaknesses to remediate and settings to improve.
-
Modular Architecture
Audit checks can be enabled one-by-one for each individual target. Users can develop custom, system-specific checks either themselves, or with the assistance of Silent Signal experts.
-
Zero Dependencies
Security checks can be launched from workstations or servers, from Linux or Windows. No additional software is required on the target systems.
-
Time Well Spent
Clear issue descriptions and prioritization of findings based on hands-on offensive experience ensure that defenders will work on solving the right problems.
-
Supporting the Security Process
Flexible export formats allow easy delivery of findings to existing risk management systems. Guided questionnaires help the security team to obtain accurate information from system operators.
Security awareness board game
Our own cooperative security awareness board game can be bought as a product or as a service as well.
-
Product
-
Service
During the game, players impersonate six characters to experience the information security dangers that can affect them during an average day at work. Players must pick security awareness skills they find most important and use them as they encounter various security-related events in each round. Without proper defense, these can become incidents with attackers getting their hands on their devices, passwords, internal or sensitive information. Some attacks can be tied to certain locations or inherent traits of characters, so players must be vigilant and identify relevant infosec skills for each situation. And what's the goal? To reach the end of the workday with as many assets and pieces of information still in their possession as they can.
Awareness Game
Our online Awareness Game can help you bring a new vibe to Cyber Security Month or any other time of the year, to promote security awareness. Fans of gamification can test and improve their awareness through various challenging tasks - and may even compete with each other.
Our solution is quick and easy to deploy and helps develop security awareness for organizations who are ready to include playful ways to deepen the knowledge of information security of their users, but also need flexibility and online options.